Despite taking every precaution, IT-based systems and products are rarely completely free of security vulnerabilities. In order to detect and fix vulnerabilities and attack areas early on, software and hardware must endure rigorous security testing. However, cybersecurity researchers who report vulnerabilities responsibly and in the interest of common good (so-called “white hat hackers”) are currently at risk of criminal prosecution. The Fraunhofer Institute for Applied and Integrated Security AISEC has responded by developing an internal procedure based on best-practice processes for dealing with vulnerabilities discovered by its researchers. Fraunhofer AISEC has also collaborated with the Sec4Research interdisciplinary research team to produce a white paper suggesting ways to improve the legal situation of “white hat hackers” from within the research community.
Security researchers on legal thin ice
Under current German legislation, some of the tools and practices crucial to uncovering vulnerabilities, and by extension to the work of IT security researchers, are legally prohibited.
For example, reverse engineering is used in security testing to reveal how an unknown system or product functions and is analyzed for vulnerabilities. Under copyright law, certain forms of reverse engineering are permitted but only with the permission of the creator. However, IT systems are made of various components from different, international manufacturers. It is therefore virtually impossible on a practical level to acquire every creator’s consent. This means that reverse engineering activities pose immeasurable liability risks for cybersecurity researchers, who have considerably fewer legal resources at their disposal than the companies responsible for the products.
Coordinated disclosure procedures at Fraunhofer AISEC
Due to the lack of legal requirements, Fraunhofer AISEC has adopted a coordinated vulnerability disclosure (CVD) process that outlines how researchers should handle identified security-related vulnerabilities. This process does not fully disclose vulnerabilities to manufacturers, users, other researchers, intelligence agencies, and criminals directly (so-called full disclosure), and it also does not ignore or downplay any identified security risks. The goal is simply to find a solution favorable for users and manufacturers that prevents criminal misuse of the product vulnerability and safeguards the security of the public.
This procedure for disclosing vulnerabilities applies exclusively to vulnerabilities revealed during Fraunhofer AISEC research projects or as part of publicly funded projects. Any security concerns identified during contractual research for industry partners are confidentially disclosed solely to the customer and are not subject to the coordinated vulnerability disclosure process.
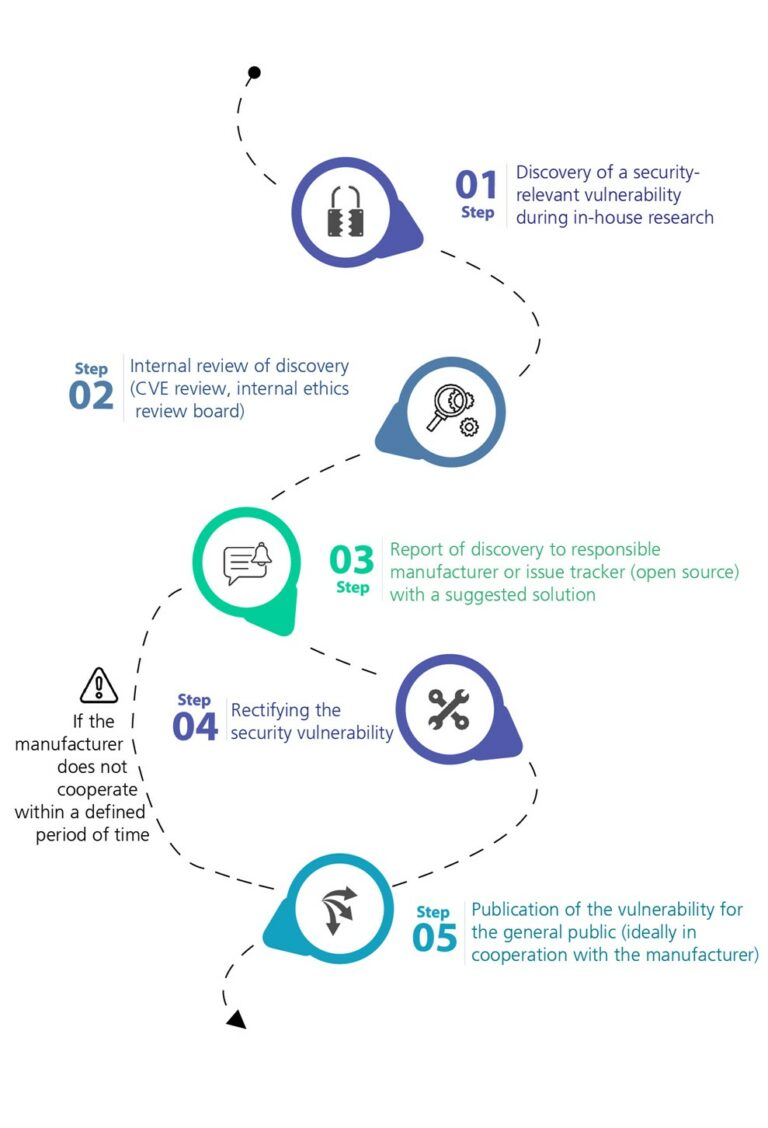
Fig. 1: Coordinated vulnerability disclosure at Fraunhofer AISEC
Step 1 and 2: Discovering and assessing a vulnerability
Any security-relevant vulnerabilities found in the course of Fraunhofer AISEC’s own research are documented internally and then checked to see if it is already entered into the CVE (Common vulnerabilities and exposures, www.cve.org) and therefore already known. The process also involves an internal ethics review board, comprising of Fraunhofer AISEC’s offensive IT security research experts. The experts do a confidential initial assessment regarding the severity of the discovered security vulnerability and can then advise the researchers and the institute’s management on how to best inform those responsible for the product.
Step 3: Report to the party responsible
If the discovered vulnerability is relevant to the security of the product, but is not yet known to the public, the responsible product manufacturers are informed. Where possible, this is followed by a concrete solution outlining ways of preventing any negative effects resulting from the vulnerability.
Meanwhile, Fraunhofer AISEC books an ID number in the MITRE Corporation’s CVE database that does not contain any specific information about the security risk. Should the responsible manufacturer be a CNA (CVE Numbering Authority) — i.e. an IT provider, security company or research institution that issues and manages CVE numbers together with the MITRE Corporation — this vulnerability is registered in the managing manufacturer’s database.
Unfortunately, only few manufacturers have established processes for receiving vulnerability reports according to ISO-Standard 30111 “Vulnerability handling processes”, making it difficult for researchers to identify the relevant contact person and submit encrypted security information about the vulnerability. We therefore advise all manufacturers to set up reporting portals and all necessary processes. We are happy to advise you on this.
The process is simpler when it comes to vulnerabilities that are discovered in open source projects. Generally, it is easier to get in touch with the developers of the software and to notify them of the issues. Furthermore, there are no criminal charges to be feared
Step 4 and 5: Rectifying the security vulnerability and publication
A security vulnerability should be rectified immediately by either the manufacturer or the operator. Fraunhofer AISEC and the manufacturer subsequently publish information about the rectified vulnerability to the public either by means of a scientific paper or a blog post.
However, if the deadline set by the ethics review board passes and no feedback has been received from the manufacturer, or there is reason to believe that no solution will be developed, then Fraunhofer AISEC publishes the vulnerability with the respective CVE reference so that users can take the appropriate precautions and prevent any damage.
This process of coordinated or responsible vulnerability disclosure, like the one implemented at Fraunhofer AISEC, is currently not supported by the German legal framework. However, these processes are vital in order to differentiate scientists acting in the public interest from cybercriminals and to ensure that research institutes can continue to develop effective protective measures against new attacks and security vulnerabilities without facing legal ramifications.
The need for legislative reforms for offensive security research
Fraunhofer AISEC teamed up with the Sec4Research interdisciplinary research team to bring attention to legislative gaps and to allow security researchers to disclose vulnerabilities safely and legally. The co-authored whitepaper compiled in 2021 explores the current legal situation surrounding the discovery and the disclosure of security vulnerabilities. In it, 22 authors call for legal clarity for IT security research, defined standards for dealing with security vulnerabilities, international cooperation as well as a clear commitment on the part of policymakers to cybersecurity research.
Fraunhofer AISEC's recommendations for action
In addition to the whitepaper, Fraunhofer AISEC proposes three practical recommended actions to ensure that vulnerabilities are disclosed in a legally compliant and responsible manner across Germany to protect those affected and reinforce the security of IT-based systems and products:
- Legalization of reverse engineering in software: While hardware can be disassembled and analyzed, software licensing terms have so far prohibited almost all attempts involving the examination of software to identify individual components and their relationships to each other. This significantly restricts the possibility of discovering security vulnerabilities and protecting users.
- Developing an independent reporting office: An independent reporting office for vulnerability discoveries is necessary for IT security researchers to be able to clearly distinguish themselves from cybercriminals and to prove their good intentions for the general public. It should coordinate and document if and when manufacturers have been notified about a vulnerability found in one of their products.
- Establishing a service organization: On top of the current legal situation, the balance between ethical hackers and the manufacturers or operators of vulnerable products is clearly skewed. An independent organization, modeled on the French Cybersecurity Advisors Network (CyAN) initiative (de) could help by providing consulting services and legal assistance to white hat hackers. At the same time, this organization could encourage an eye level exchange with large corporations and promote ethical hackers’ interests on a political level.
Politics, society and IT system manufacturers and operators must strive to create conditions which allow for the responsible and coordinated disclosure of IT security vulnerabilities, prevent damage to users and companies, and ensure that Germany continues to be an internationally competitive location for IT security research.
Additional information
» Sec4Research homepage: https://sec4research.de/english
» Fraunhofer AISEC homepage: https://www.aisec.fraunhofer.de/en.html
Autors

Marc Schink
Marc Schink carries out research in the field of “Hardware Security” at Fraunhofer AISEC. In his private life as well as at the institute, he strives to detect vulnerabilities in hardware and software. He has conducted several vulnerability disclosure processes with renowned and international manufacturers.
Contact: marc.schink@aisec.fraunhofer.de

Dieter Schuster
Dieter Schuster works in the research department “Product Protection and Industrial Security” at Fraunhofer AISEC. He coordinates the field of Offensive Security and Penetration Testing.
Contact: dieter.schuster@aisec.fraunhofer.de









One comment
Great! Nyanyanyanyanyanyanya!