The work on gallia was partly funded by the German Federal Ministry of Education and Research (BMBF) as part of the SecForCARs project (grant no. 16KIS0790). A short presentation and demo video are available on YouTube.
Disclaimer: Keep in mind that this project is intended for research and development usage only! Inappropriate usage might cause irreversible damage to the device under test. We do not take any responsibility for damage caused by the usage of this tool.
Metadata
tl;dr:
- FOSS: https://github.com/Fraunhofer-AISEC/gallia
- PyPI: https://pypi.org/projects/gallia
- documentation: https://fraunhofer-aisec.github.io/gallia/
- license: Apache 2.0
- maintainers: Stefan Tatschner (@rumpelsepp), Tobias Specht (@peckto)
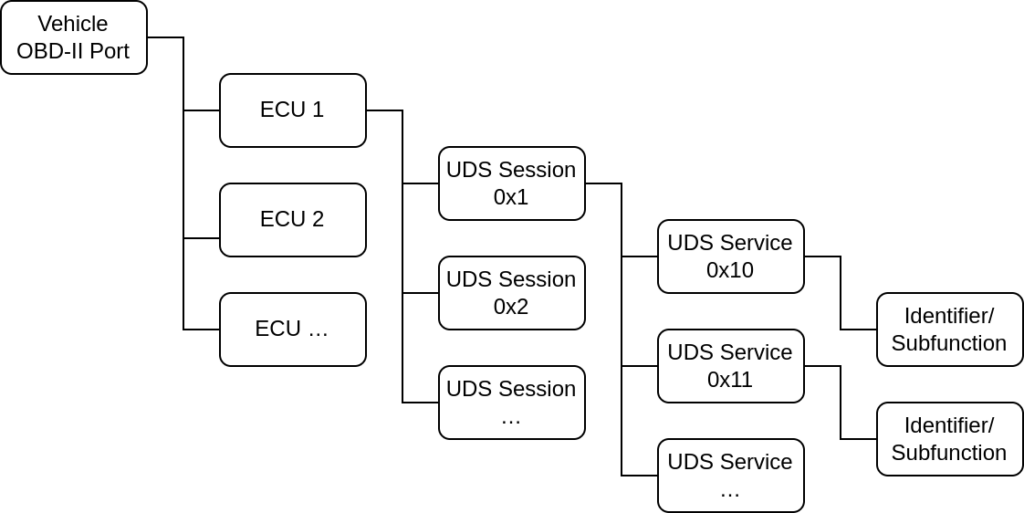
Architecture
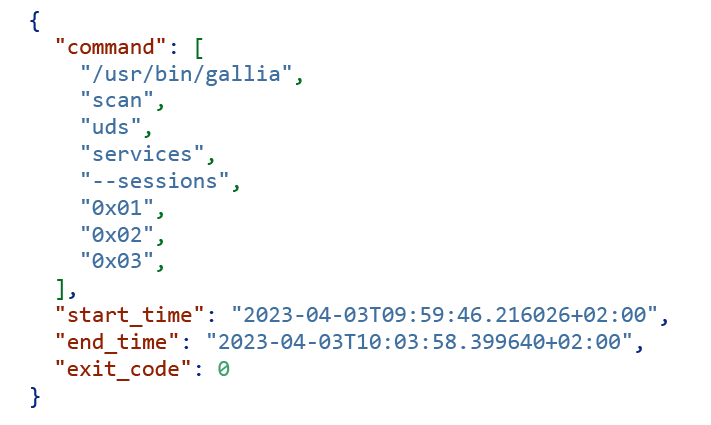
Test runs

- command line invocation,
- process environment,
- start of test,
- end of test,
- exit code, and
- JSON formatted log file.
Software Architecture

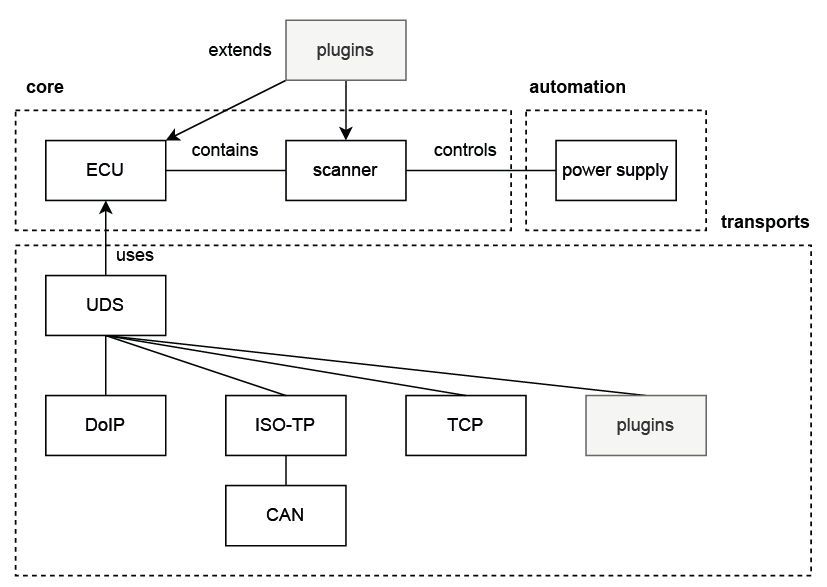
The core component is divided into multiple, logically separated blocks:
- core: The software core provides basic functionality. Used by the scanner.
- transports: Implementations of relevant network protocols, in this example UDS, DoIP, et cetera. The transports module can be extended via plugins.
- automation: Modules that implement triggering power supplies enabling power cycles during a scan.
Use Case
Command Line Interface
Future Work
- Additional transports: Currently, there are only a few generic and UDS specific transports implemented. A few ideas for additional transports are: subprocess, ssh, http, …
- Additional scanners: Currently there are only UDS specific scanners available. gallia could benefit from more general scanners that e. g. perform more different discovery scans. Examples are DLT or XCP which are used in automotive networks as well.
- Split gallia into a core library and a collection of scanners: This would reduce dependencies for projects willing to use the test run concept.
Authors

Stefan Tatschner
Stefan Tatschner joined the Fraunhofer AISEC in 2015. His research focus is penetration and software testing in the automotive domain. Together with his college Tobias Specht, he maintains the gallia project.
Contact: Stefan.Tatschner@aisec.fraunhofer.de

Tobias Specht
Tobias Specht is an IT security researcher in the field of penetration testing and static code analysis with a focus on the embedded and automotive domain. He has been working at Fraunhofer AISEC since 2018 and has contributed to industry and research projects such as the gallia framework. Together with his colleague Stefan Tatschner, he is maintainer of the gallia project.
Contact: Tobias.Specht@aisec.fraunhofer.de