A new hope for better and more secure OT systems
Ensuring security often means running security tests or rolling-out new security controls on a system. Maintaining a high or even sufficient level of security is challenging, especially when the protected system is required to operate in the field for a long period of time, for example up to 25 and more years in manufacturing. A digital twin may very well be the solution: It allows you to do a lot of security testing before even touching the real system [1]. This security testing can include automatic, periodical testing or penetration and system testing. A system can be checked for hardware and software misconfigurations. Running these tests on the digital twin gives you the benefit of a more realistic estimation on how the system might behave in real life. Furthermore, damage done to the digital twin does not affect operation as the twin can be easily reset. Another prominent use case for digital twins in OT security are intrusion detection and prevention systems that monitor networks for malicious activity. As large amounts of data are required for training their detection mechanisms, digital twins can produce that data and help in training the intrusion detection systems before deployment.
True digital twins are hard to find
Admittedly, the application of digital twins for improving security (and for general purposes) is currently limited. A proper digital twin requires a continuous stream of high-resolution data. This stream of data comes from multiple sources and is changing during the life cycle of the system. Initially, the data may stem from engineering and development tools; later, it may come from the deployed system during its operation in the field. Data of sufficiently high resolution and in adequate quantity (speaking of big data) is key for many use cases in digital twinning. In research, there are many testing environments that use simulation techniques to mimic a real-life counterpart [2]. However, it is hard to find an evaluation that really shows how closely they mimic their real-life counterpart [3]. Finding a method to achieve a sufficiently high level of data resolution (known as fidelity) is a research question that remains to be solved – at least for the moment. This should be kept in mind when considering possible applications of digital twins for OT security. It appears to be a computer or network engineering challenge as well as an organizational challenge that needs to be tackled before talking about security in greater detail [4].
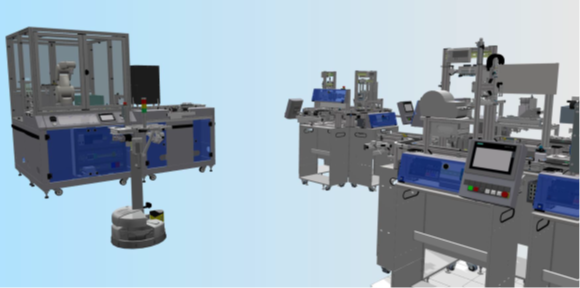
Fig. 1: Simulation of our production line at Fraunhofer AISEC used to study digital twins.
Future research directions - a step-by-step approach
Since digital twins are rare at this time, different methods can be considered when developing digital twins [5]. Our goal are developments towards digital twins that are beneficial to OT security. With this in mind, we outline a possible development roadmap.
As not all parts of a complex system, e.g., as seen in Figure 1, are equally relevant for studying a given use case, different levels of data resolution can be applied to different system components. An example for this is penetration testing of programmable logic controllers (PLCs) as seen in Figure 2. The twins of PLCs need to mimic the real device more accurately than device twins that are not directly the target of the test. This varying level of realism can be realized with a variety of techniques such as emulation or virtualization. Given further improvements in big data acquisition from industrial environments, digital twins can emerge from that in the future.

Fig. 2: OT equipment of our production line at Fraunhofer AISEC.
[1] Eckhart, M., & Ekelhart, A. (2019). Digital twins for cyber-physical systems security: State of the art and outlook. Security and Quality in Cyber-Physical Systems Engineering, 383-412.
[2] Ani, U. P. D., Watson, J. M., Green, B., Craggs, B., & Nurse, J. R. (2021). Design Considerations for Building Credible Security Testbeds: Perspectives from Industrial Control System Use Cases. Journal of Cyber Security Technology,5(2), 71-119.
[3] Kayan, H., Nunes, M., Rana, O., Burnap, P., & Perera, C. (2022). Cybersecurity of industrial cyber-physical systems: a review. ACM Computing Surveys (CSUR), 54(11s), 1-35.
[4] Giehl, A., Wiedermann, N., Gholamzadeh, M. T., & Eckert, C. (2020, August). Integrating security evaluations into virtual commissioning. In2020 IEEE 16th International Conference on Automation Science and Engineering (CASE)(pp. 1193-1200). IEEE.
[5] Jones, D., Snider, C., Nassehi, A., Yon, J., & Hicks, B. (2020). Characterisingthe Digital Twin: A systematic literature review.CIRP Journal of Manufacturing Science and Technology,29, 36-52.
Additional Information
- Results of the research projects IUNO and IUNO Insec
https://iuno-projekt.de/ (in German) - PoQsiKom Project Launch. Post-quantum secure communication for Industry 4.0 11.04.2022
https://www.aisec.fraunhofer.de/en/media/press-releases/2022/PoQsiKom.html - Peter Koller. Sicherheit in der Automatisierung. Damit der Digital Twin nicht zum bösen Zwilling wird. 15.09.2022
https://www.all-electronics.de/automatisierung/damit-der-digital-twin-nicht-zum-boesen-zwilling-wird-833.html
Author

Alexander Giehl
Alexander Giehl has worked at Fraunhofer AISEC since 2013, where he specializes in improving cybersecurity via modelling and simulation. He focuses on secure embedded systems, security in manufacturing and automotive, digital twins, as well as general cybersecurity and management systems. In addition, he supervised the research project »IUNO Insec« developing cybersecurity solutions for SMEs funded by the German Federal Ministry of Education and Research (BMBF).
Contact: alexander.giehl@aisec.fraunhofer.de








