Challenges for cryptographic processes
In the digital world, the authenticity and integrity of data is essential. For example, it is important to ensure that the firmware and software on a device come from a trustworthy source and have not been manipulated or substituted. This is usually achieved using signatures, which are verified in the secure boot process when the system starts up. The code will only be executed if verification is successful.
To ensure that the data is secure and the information remains confidential, cryptographic processes such as signatures need to be able to withstand various attack paths. One verification method is cryptanalysis, where mathematical and statistical relationships between the input and output values of an algorithm are used to draw conclusions about the secret key.
One subdomain of cryptanalysis is potential attacks using quantum computers. They enable further cryptanalytic attack paths, because conventional signature processes are based on mathematical problems that can be broken with potential powerful quantum computers. The necessary technology is still in the development stage, but it is assumed in expert circles that it will have significant impacts on IT security in the near future.
For this reason, major efforts are currently being made to develop and implement quantum-secure processes, also known as post-quantum cryptography (PQC).
Fraunhofer AISEC is contributing to research into new quantum-resistant cryptographic methods with its Competence Center for Post-Quantum Cryptography.
No successful attacks of this type are known in the case of the WOTS-based signature processes investigated in the Fraunhofer AISEC study.
However, as they are used in embedded devices in particular, they are exposed to another kind of attacks: hardware attacks.
This type of attack targets the implementation of the algorithm on the actual hardware. Here, the physical properties of the architecture and the effects of the operations play an important part. There are various attack options, from passive observation and analysis of intermediate values to invasive attacks with manipulations such as skipping operations.
Study of laser-based fault attacks on XMSS
This study was commissioned by the German Federal Office for Information Security (BSI) and carried out at Fraunhofer AISEC. In the study, a laser-based fault attack was used on the XMSS signature scheme used to verify the authenticity and integrity of the firmware in a quantum-secure way.
The attacked XMSS quantum-secure signature scheme is based on the WOTS process, which also forms the basis of other cryptographic signature methods such as LMS and SPHINCS+. Both XMSS and WOTS use hash functions to guarantee their security. It is important to note that this is a stateful signature process. In practice, it is mainly used to verify data that rarely changes, for example in the boot process of an embedded system.
Theoretical preparatory work lays the foundation for the investigations
This work is based on a research paper by Fraunhofer AISEC. In it, Alexander Wagner and his team have shown how a fault attack on a hash-based signature process can work.
On the one hand, faults were introduced into the signature generation in order to be able to infer parts of the secret key. This allows attackers to generate forged signatures that can get past verification.
On the other hand, faults were introduced into the signature verification process to prevent a fake signature from being recognized as not genuine. In the study, which has now been published by the BSI, the second attack was demonstrated in practice.
Fault attacks change intermediate values and disrupt the calculations
As part of the project, an active side-channel attack on a standard microcontroller was demonstrated.
The first step was to prepare the target and analyze it more closely. The zones that were relevant to an attack were identified using infrared images of the chip. Targeted laser pulses were used to manipulate intermediate values in the SRAM to change the result of the calculation. Using analyses of the faults triggered, a fault model was developed for the chip to change a targeted value.
It was then shown that it is possible to introduce a targeted fault into the calculation of the checksum — a mathematical checksum used to validate the integrity of the data in a signature — resulting in a fake signature being categorized as valid by the firmware.
Compared to other work with laser-based fault attacks, the time window for introducing the fault in this attack model was particularly large.
Attacks raise awareness among manufacturers and developers
In the work by Fraunhofer AISEC, targeted countermeasures were discussed and proposed to prevent this kind of attack path.
A countermeasure with a negligible overhead relative to the total duration of the calculations is the repeated calculation and verification of the checksum. Using this easy-to-implement countermeasure makes attacks of this kind significantly more difficult because any manipulation of the checksum will be detected.
The publication will educate a wide audience about the attacks.
This will allow manufacturers and developers to identify and improve these kinds of potential vulnerabilities as early as the product development stage.
Overall, this work is a key cornerstone of the understanding of what implementations of hash-based signature processes should look like in practice.
Pictures
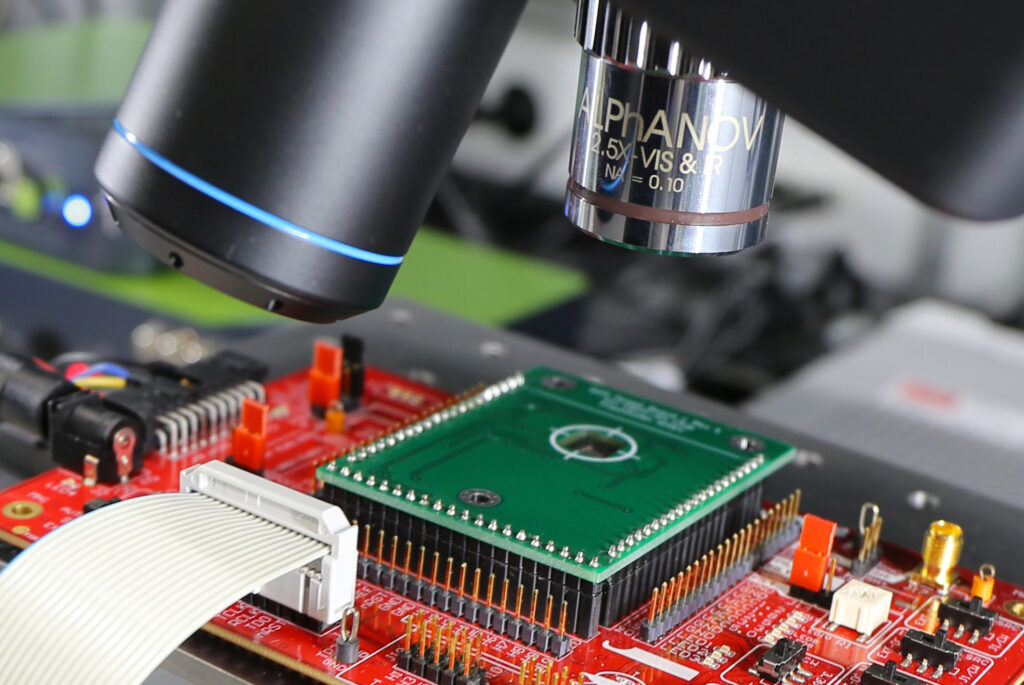
Figure 1: Using the ALPhANOV laser setup, brief laser pulses are injected into the target device to generate faults in the calculation.
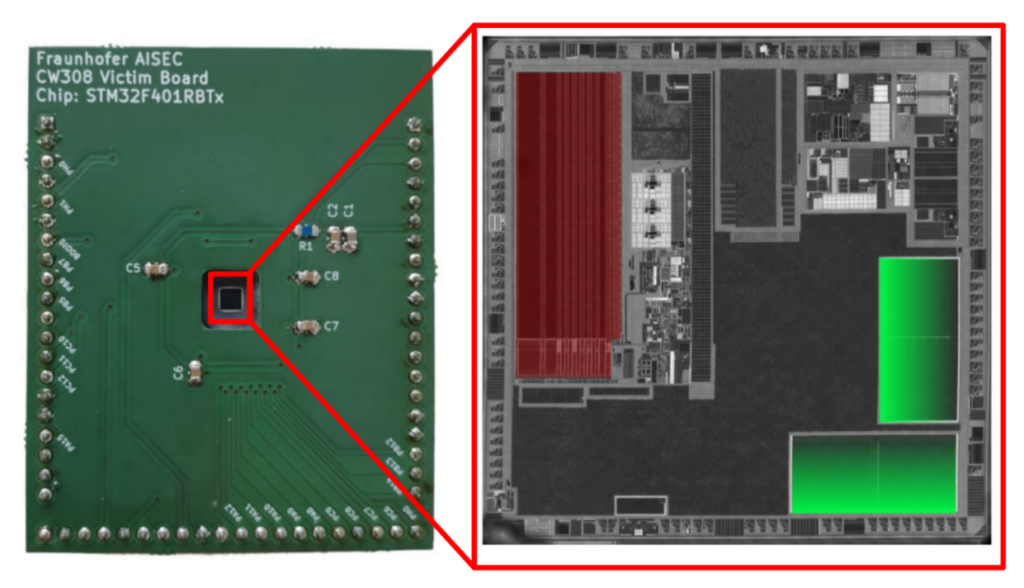
Figure 2: The areas of the target device can be assigned using an infrared image of the target chip. The flash memory is shown here in red and the SRAM in green.
Authors

Silvan Streit
Silvan Streit has been conducting research as a research scientist in the Hardware Security department at Fraunhofer AISEC since 2019. His core area of expertise is side-channel security of post-quantum cryptography, with a particular focus on the development of new attack vectors. In this area, he relies on his prior knowledge in information field theory and in secure and efficient implementations of lattice-based cryptography.
Contact: silvan.streit@aisec.fraunhofer.de

Marc Schink
Marc Schink conducts research in the Hardware Security department at Fraunhofer AISEC. His focus is on identifying vulnerabilities in hardware and software. He has already carried out multiple vulnerability report procedures on products by reputable national and international manufacturers.
Contact: marc.schink@aisec.fraunhofer.de

Alexander Wagner
Since 2018, Alexander Wagner has been a research scientist in the Hardware Security department of Fraunhofer AISEC. His research focuses on the secure and efficient implementation of hash-based signature processes. He also works on the implementation of side-channel analysis and fault attacks in the laboratory, as well as its limitations.
Contact: alexander.wagner@aisec.fraunhofer.de